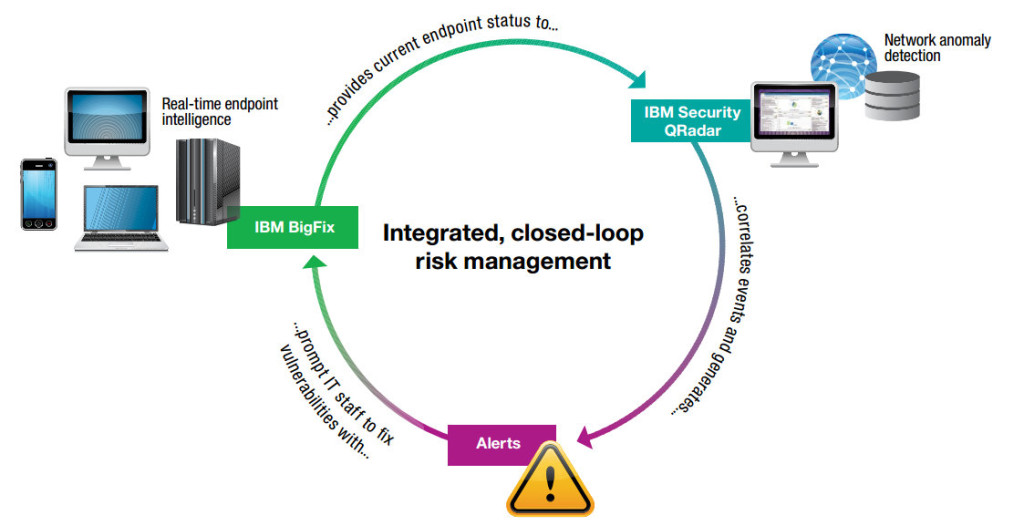
How IBM BigFix and IBM Security QRadar work together to fill in the gaps of cybersecurity
With today’s advanced threats growing stealthier, more dynamic and more damaging, the need for integrated, intelligent, automated resources has never been greater. BigFix and QRadar Security Intelligence Platform can help meet this need. They empower IT operations and security teams to work together to protect assets from increasingly sophisticated attacks.
The following examples show how BigFix and IBM Security QRadar solutions can be used together to strengthen security.
Identify
Cybercriminals are continuously using new tactics to attack endpoints, and these advanced threats can often go unnoticed by traditional security approaches such as anti-virus and antispyware solutions. But with granular visibility into endpoint properties, BigFix enables organizations to see “stealthy” configuration changes and automate remedial action. Similarly, BigFix can discover suspicious applications. When a piece of malicious code attempts to install unauthorized applications, BigFix has the ability to identify that behavior in real time and automatically remediate it.
QRadar users can leverage this endpoint intelligence to help IT staff focus on the vulnerabilities that do not have an automated fix. In fact, IBM Security QRadar Vulnerability Manager helps minimize false positives and filters out vulnerabilities that have already been classified as non-threatening. For example, applications may be installed on a server, but they may be inactive, and therefore not a security risk; devices that appear exposed may actually be protected by a firewall; or endpoints that have vulnerabilities may already be scheduled for patching. BigFix continuously assesses the status of endpoints, automatically initiating updates and configuration changes via IBM Fixlet® messages. By understanding which vulnerabilities have a Fixlet available, QRadar users can drastically reduce the total number of vulnerabilities that need to be analyzed— improving the response and remediation time for unpatched vulnerabilities. What’s more, IT staff can use ad-hoc queries to help identify offenses and suspected incidents.
Analyze
When unusual activities are taking place anywhere on the network, QRadar users can correlate that suspicious behavior with other threat data and assign the high-risk vulnerabilities to BigFix for remediation. This way, IT personnel can not only know which updates, changes or patches are considered high priority, but can also take action on them—helping reduce the risk of the initial exploit, lowering exploit propagation and improving productivity. Closed-loop verification helps ensure that changes are completed and the status is reported to the management console.
Whether applying a patch to repair a newly discovered vulnerability on hundreds of thousands of endpoints or assessing the configuration status of employee-owned devices, BigFix can affect organization-wide change in minutes. With BigFix, assessment and analysis are conducted on the endpoint itself—which increases the speed of discovery, software delivery and validation. Less communication is required between the management server and endpoint, increasing speed and reducing the amount of network bandwidth consumed.
Action
BigFix can accurately interrogate any aspect of an endpoint and provide a real-time view into problems that exist in the environment. For example, BigFix can detect when users are using modified “jail-broken” devices or have installed suspicious applications, and can then quarantine the device from the network. This enables organizations to discover issues quickly, and it provides an additional layer of defense when traditional security defenses either fail or provide fixes too late to prevent an incident.
In addition, QRadar users can easily combine mobile events from BigFix with network activity for offense identification, forensics investigations and compliance reporting. With more accurate asset information, IT staff can rapidly identify rogue or unmanaged endpoints, improving detection and response time. QRadar also maintains a current network view of all discovered vulnerabilities, including which vulnerabilities are currently blocked from exploitation by firewall and intrusion prevention system (IPS) rules, and which are still at risk of being exploited.
If users have installed a virus, BigFix can ensure that endpoints are disinfected and stay up to date. The solution’s centralized management console provides a single, granular view for comprehensive visibility and control across distributed global networks. Operators can perform remedial actions in minutes— and receive immediate validation that the action has completed successfully
Monitor
QRadar solutions and BigFix can work together to provide continuous policy enforcement to help maintain compliance. In fact, BigFix provides organization-wide reports instantly— without having to poll systems to assess the overall security compliance posture. This data can then be included within out-of- the- box QRadar compliance reports, including historic views of daily, weekly and monthly trends, as well as long-term trending reports required by many security regulations.
With a single, integrated dashboard for viewing multiple vulnerability assessment feeds and threat intelligence sources, QRadar users can understand the overall context of network usage, security and threat posture. This helps facilitate compliance— including CyberScope reporting and continuous diagnostics and mitigation programs—by prioritizing security gaps for resolution. It’s an integrated approach to addressing vulnerabilities and then reporting on the up-to- the- minute security status.
Control
With the help of QRadar solutions and BigFix, IT operations and IT security teams can more easily collaborate on suspected offenses, initiating investigations and corrective actions from the same console. This can help speed the response to web-based malware and other types of advanced threats. Operations staff can be overwhelmed by a sea of vulnerabilities—without the contextual data to help them focus their efforts on the weaknesses that are most likely to be exploited. It is not uncommon, as a result, for several weeks to pass between the discovery of a known vulnerability and the known patch being applied. At the same time, security teams can lack a comprehensive view of endpoint status, which limits their understanding of the threat landscape. And, if an endpoint vulnerability is identified, security teams can find it nearly impossible to quickly remediate or mitigate the risks.
BigFix can provide security for fixed, network-connected endpoints and roaming, Internet-connected endpoints faster than waiting for a vendor’s mass-distribution of signature files. BigFix cross-references threat information against a large, continuously updated cloud-based database to assess the malicious potential of files and URLs in real time, and delivers anti-malware protection to endpoints as needed. A laptop used in an airport, for example, can receive anywhere, anytime, cloud-based protection from threats lurking on websites it visits or files it receives.
In Summary
By combining BigFix with QRadar Security Intelligence Platform, organizations can be proactive about vulnerability management. They can identify weaknesses in systems, software or the network that attackers can exploit—and then remediate those vulnerabilities to prevent an attack or minimize the impact to the organization.
If you liked this blog, you also might like: Smarter Security, Smarter Everything
IBM Security: QRadar Intelligence and Ops
IBM's integrated solutions harness security-relevant information from across your organization, and use analytics and automation to provide context and help you detect threats faster, identify vulnerabilities, prioritize risks, perform forensics analysis and automate compliance activities. 
-
IBM QRadar Security Intelligence Solutions Grow As Your Needs Grow
-
Organizations today need integrated security intelligence solutions that can grow as their business grows, both in terms of size and capabilities. The IBM QRadar Security Intelligence Platform meets these requirements by providing an integrated security solution that is highly scalable, and can expand it’s capabilities to meet increasingly hostile security challenges. This short video describes how IBM Security QRadar delivers scalability, visibility, vulnerability management, risk management, and performs forensics analysis to help you quickly and efficiently detect and respond to security threats. To learn more, please visit http://ibm.co/1HNzm2n
-
Video: Don’t Drown in a Sea of Cyberthreats: Mitigate Attacks with IBM BigFix & QRadar
-
Security teams can be overwhelmed by a sea of vulnerabilities–without the contextual data to help them focus their efforts on the weaknesses that are most likely to be exploited. Cyberthreats need to be stopped before they cause significant financial and reputation damage to an organization. You need an endpoint security platform that can detect threats, prioritize risks and respond within minutes to shut down an attack or vulnerability that could compromise your endpoints.IBM BigFix seamlessly integrates with IBM QRadar to provide closed loop vulnerability management, accelerating risk prioritization and incident response to mitigate potential attacks giving you an integrated threat protection system to keep your endpoints and data secure.For more information, please visit http://ibm.co/1oSThIF
-
Report: IBM X-Force Threat Intelligence Report 2016
-
In the modern era of mega breaches, there seems to be an ever-upward trend of more attacks, more leaked records and more varied threats. Yet, by the numbers, 2015 was not a complete disaster. While significant interruptions, shifts in perspective and challenges to the security industry continue to evolve, there are some areas of slowed growth and even improvement. This paper takes a look at some of the notable highlights from 2015 and makes some projections at what we might glean for the future.
-
How IBM Helps Secure the Cloud
-
IBM Security helps customers secure public, private and hybrid clouds. With IBM Security customers can manage user access to cloud applications and protect the data that lives in the cloud. Customers can use IBM Security products like QRadar to gain full visibility into security threats facing their organization.For more information, please visit http://ibm.co/1zlRM6Y
-
Benefits of Security Intelligence on Cloud
-
Watch this short video and listen to Vijay Dheap, IBM Global Product Manager for Security, describe the benefits of Security Intelligence on Cloud, a new offering from IBM. These include lowering costs, increasing efficiency, shifting from a CapEx to an OpEx model, and improving compliance and reporting. Vijay also touches on the advantages of incident forensics and the rapid analysis of security offenses. For more information, please visit http://ibm.co/1zlRM6Y
-
KocSistem Replaces Their SIEM & Deploys QRadar For Log Management & Regulatory Compliance
-
Many organizations are challenged with meeting regulatory compliance mandates. Watch this video and learn how Ko?Sistem, one of the largest IT services companies in Turkey, is complying with regulations using IBM Security QRadar. You will hear about how they removed a SIEM from another company and installed QRadar, and lowered costs, improved performance, and benefited from greater ease of use.For more information on QRadar, please visit: http://ibm.co/1DFd42q
-
The Next Era for Security – IBM QRadar Security Intelligence Platform
-
“IBM QRadar Security Intelligence Platform provides real-time transparency to see better into your organization than ever before,” says Steve Robinson, Vice President, IBM Security Division. Implementing the security information and event management (SIEM) dashboard, the IBM QRadar platform brings security operations teams full visibility through a single window. It also automates the tedious task of vulnerability management. Security teams can spend less time on manual tasks and more time on network security assessments. This means, according to Robinson, “QRadar will probably pay for itself right out of the gate.”For more information on Security Intelligence go to: http://ibm.com/software/products/us/en/subcategory/SWI60For more information on IBM Security: http://ibm.co/ibmsecurity
-
IBM Security Intelligence for the Cloud with QRadar
-
IBM QRadar Security Intelligence helps you monitor the cloud for security breaches and compliance violations using advanced security analytics. Using a flexible deployment architecture and connectors to popular cloud services, IBM QRadar Security Intelligence provides deep visibility of threats across both on-premise IT and hybrid cloud deployments.To learn more, please visit http://ibm.co/1DwamZk
-
How to Investigate Security Incidents Quickly and Easily
-
What’s behind a cyber attack? Gaining insight and clarity into the what, when and how of an enterprise security incident: IBM Security QRadar Incident Forensics helps you win the race against time when a security breach occurs by allowing you to rapidly and easily perform in-depth security incident investigations. It provides visibility and clarity to potentially malicious activity by thoroughly analyzing packets captured from your network, and in most cases can help resolve security incidents in minutes or hours instead of days or weeks. It is integrated with IBM Security QRadar solutions, allowing the same person who has visibility to logs and network flows to conduct searches and learn more about an incident. With QRadar Incident Forensics, security staffs can analyze many types of data, understand their relationships, re-trace the steps of an attacker, remediate damage, and reduce the chances of a recurrence. Learn more about QRadar Incident Forensics: http://ibm.co/QrSCg3
-
IBM Security QRadar and iSecure Work Together to Improve Customer Security
-
This short video describes the benefits that customers receive from the IBM Security QRadar and iSecure partnership. iSecure wraps their services around IBM’s QRadar products and helps clients address their security gaps. iSecure chose IBM because of the visibility QRadar provides to security exposures, and IBM’s continued investment in new capabilities such as vulnerability management, risk management, and incident forensics. iSecure also endorses IBM ability to provide a solution that combines multiple point products into a single, consolidated security solution.Learn more about IBM Security: http://ibm.co/ibmsecurity
-
Local Government Secures Their Data With QRadar
-
Securing people and funds is a challenge for the public sector. With these limited resources, IT departments must choose a security tool set that will be easy to implement as well as easy to manage. In this video, a local government explains why they chose IBM Security’s QRadar and how it has been a true asset to their work process.To learn more about QRadar, please visit http://ibm.co/1HNzm2n
-
Quickly Investigate & Resolve Security Events with QRadar Incident Forensics
-
When you make intelligent analytics part of your IT security strategy, you gain access to the tools to quickly identify and stop network security breaches, before real damage is done. IBM QRadar Incident Forensics helps security professionals reduce time spent on manual searches to identify a true threat, quickly analyze and stop the attack, and reconstruct the incident to gain the knowledge to prevent a similar attack in the future. To learn more, visit http://ibm.co/15NUhEI