For today’s connected businesses, cybersecurity is not optional: it’s an integral piece of the formula for sustained business success.
The only problem is, cybersecurity is complex and nuanced. It requires levels of specialization and breadth of knowledge that many businesses struggle to staff. And the threats are always changing and evolving.
Managed security services are one solution to this business challenge. Businesses gain specialization and breadth without hiring internally and peace of mind knowing they’re prepared 24/7 — no matter what happens next.
What Are Managed Security Services?
Managed Security Services (MSS) are network security services that have been outsourced to a service provider. This service provider, known as a Managed Security Services Provider (MSSP), oversees and administers a company’s security processes with the aim of reducing the risk of cyber threats and data breaches.
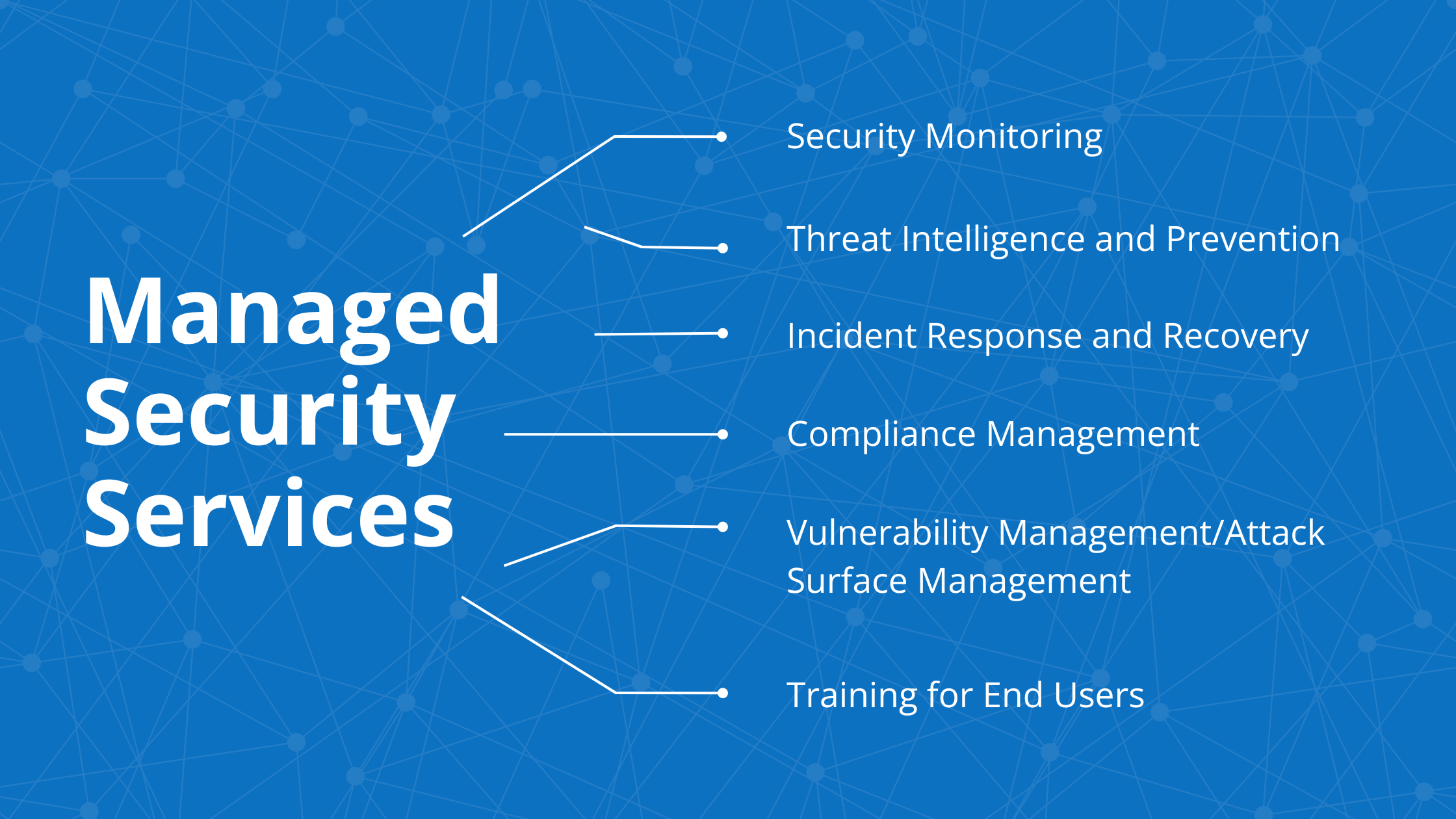
Managed Security Services can cover a broad range of functions, including but not limited to:
- Security Monitoring: MSSPs continuously monitor a company’s networks and systems for any suspicious activities or potential threats. This often involves the use of Security Information and Event Management (SIEM) systems that aggregate and analyze event data in real time.
- Threat Intelligence and Prevention: MSSPs leverage the latest threat intelligence data to identify and block potential security threats before they can impact a business. This includes detecting and mitigating threats such as malware, ransomware, and phishing attacks.
- Incident Response and Recovery: In the event of a security breach or cyber attack, MSSPs provide rapid response services to mitigate the impact and aid in the recovery process. This might include isolating affected systems, removing the threat, and restoring sensitive data and services.
- Compliance Management: MSSPs offer compliance expertise with various industry and regulatory standards related to data security and privacy. This includes helping to create and implement necessary security policies and procedures, and conducting regular audits to ensure ongoing compliance.
- Vulnerability Management/Attack Surface Management (ASM): MSSPs regularly scan a company’s systems and networks to identify any potential vulnerabilities that could be exploited by cyber criminals. Once identified, these vulnerabilities are patched or otherwise mitigated to reduce the risk.
- Training for End Users: MSSPs provide training to end users, particularly on identifying risks in email communications. They conduct ongoing campaigns to assess the effectiveness of user training and identify individuals who may need additional training to prevent bad actors from gaining access to the network.
Choosing the Right Managed Services Provider
How should a business go about choosing a managed security services provider? Here are a few quick tips:
- Focus: Look for a partner where security is a main focus, not an afterthought.
- Industry History: Investigate whether an MSSP has successfully served others in your industry.
- Service Depth: Evaluate the MSSP’s resources. Do they have enough staff to offer 24/7 coverage? What’s their guaranteed response time, and what is their average response time?
- Compatibility: Check whether the MSSP works well with the hardware and cloud services you’re already using. Are your existing tools integrated/communicating with each other?
- Security Certifications: Does the MSSP employ staff with military or three-letter agency backgrounds? Is the staff US based? Are they available 24×7?
- Comprehensive Coverage: Make sure the MSSP can cover all aspects of your infrastructure (servers, desktops, tablets, phones) and provide a full security stack (patch management, EDR, XDR, SIEM, SOAR).
- Location and Redundancy: Where is the MSSP’s infrastructure located, and is it redundant? It’s nice to work with a provider that has a centrally located security operations center (SOC), but if something happens at that location, you need redundancies and cloud contingencies to continue operations.
- Effective Use and Knowledge of Security Tools: It’s not uncommon for businesses to have security tools in place but lack the expertise to use them effectively. This is what we often refer to as ‘shelfware’ – tools that exist within an organization but are underutilized or not used at all. A managed service provider like Flagship Solutions Group, for example, will ensure that the potential of every security tool is maximized, and nothing is left to gather dust on the shelf.
Top 6 Benefits of Managed Security Services

What can managed security services do for your business? Consider these benefits of choosing a managed security solution.
1. Access to Highly Skilled Security Professionals
Many businesses, especially small- and medium-sized businesses, don’t have the capacity, bandwidth, or security expertise to manage IT security in a comprehensive way. On top of that, qualified experts are hard to find and costly to hire, and you need expertise across a wide range of disciplines and functions.
Working with a managed security service provider is an ideal solution: it means gaining vital direct access to security experts with specialized training in areas like cybersecurity services, security operations center, intrusion detection, security audits, and incident response.
Third-party providers stay on the cutting edge of cybersecurity trends, technologies, and latest cyber threats, providing an invaluable resource for securing your business.
2. Threat Detection and Prevention
Digital threats to your business can target nearly any part of your business. It’s not enough to know that an attack happened; you need the ability to detect threats as they happen—and to prevent them from occurring in the first place.
Threat detection and prevention plays out in various ways across your business. Here are six facets to consider.
Securing Your Hybrid Cloud Environment
When organizations adopt a hybrid cloud environment as part of their digital transformation, their cybersecurity risk expands. You must address threats targeting both on-premises and cloud deployments.
Engaging a suitable managed security services provider provides access to cybersecurity professionals who specialize in complex network and cloud environments. These experts ensure ongoing protection and keep security measures up to date.
Rapid Incident Response and Recovery
When you leave your security services to a generalist in-house team, you don’t get rapid response and recovery. The initial response might be speedy, but think of the time it takes for that team to 1) figure out what the problem is; 2) determine whether they can fix the problem internally; and — when the answer to #2 is no — 3) find an outside expert who can come solve the problem.
Worst of all, once you get to #3, you’re at the mercy of those outside experts’ own availability and scheduling.
When you partner with a managed security service provider, you get a dedicated team of experts, faster incident response and a more focused solution, leading to quicker recovery times.
Proactive Risk Management
Managed security services providers excel in proactive risk management by identifying and addressing potential risks and vulnerabilities before they can be exploited. Through continuous assessment of infrastructure and security controls, they stay ahead of potential threats.
For example, in the case of disaster recovery, understanding specific risk factors based on location, business activities, and physical assets allows tailored risk management strategies.
Minimize Cybersecurity Risk
Building a well-designed system with multiple layers of security minimizes cybersecurity risks. While breaches may still occur, a robust system limits the extent of damage, turning potential catastrophes into minor disruptions.
Protecting IT Infrastructure (Network and Compute)
Protecting your IT infrastructure is more critical than ever, including compute resources and the underlying network connecting these resources and enabling business operations.
- Network Security: MSSPs analyze the packets flowing on your network to identify potential threats and gain insights into the source and destination of any potential risks. This helps in detecting and mitigating unseen threats and enhancing overall network security.
- Compute Security: MSSPs monitor and update servers, workstations and mobile devices, mitigating vulnerabilities that cyber threats could exploit across physical and virtual resources.
Ability to Obtain Cybersecurity Insurance
Insurance providers often assess a company’s security posture when determining the eligibility and premiums for cybersecurity insurance policies. They look favorably upon businesses that demonstrate strong, proactive cybersecurity measures.
When you have these elements lined out in your managed security services contract, it becomes easier to obtain cybersecurity insurance (because in the insurers’ eyes your risk profile is lower.)
3. Data Recovery & Resilience
When disaster strikes — whether that’s a literal disaster like a hurricane or a flood, or “oops I just deleted all the files” — how confident are you that your business can recover its data and continue?
Think for a moment just how serious, even existential, of a problem it would be if all your business data were suddenly gone. Could you rebuild? Would there be any customers left to rebuild for?
A reliable MSSP will make sure you have a strong backup and disaster recovery and business continuity and resilience plan in place.
4. Maintain Data Privacy Compliance
If your business handles customer data of any type, you’re likely bound to certain regulatory compliance standards. MSSPs assist businesses in maintaining data privacy compliance by:
- Assessing compliance status: Conducting comprehensive assessments to identify compliance gaps.
- Implementing necessary measures: Enforcing technical and administrative measures for compliance.
- Monitoring ongoing compliance: Providing continuous monitoring and issue resolution.
- Staying updated with regulations: Keeping track of evolving data privacy laws and advising on necessary adaptations for compliance.
5. Identity Access Management
Identity and access management, or IAM, gives users a secure way to access company resources, no matter where they’re doing their work. IAM includes processes for identity verification, authentication, authorization, and access control. In essence, it ensures that the right people have the right access to the right resources at the right times, and for the right reasons.
IAM as part of managed security services offers the following benefits:
- Enhanced Security Controls: Strong authentication and granular access controls protect against unauthorized access.
- Centralized User Management: Efficient user provisioning, deprovisioning, and access rights management.
- Compliance and Regulatory Requirements: Helps meet data privacy and security regulations.
- Improved Productivity and User Experience: Single sign-on reduces the need to remember multiple credentials.
- Rapid User Onboarding and Offboarding: Automates user provisioning and access revocation.
- Scalability and Flexibility: Adapts to organizational growth and technology changes.
6. Securely Adopt New Technologies & IoT
New technologies hit the market every single day. Some of them could facilitate your business’s next breakthrough. Others are a distraction or, worse, a threat.
It can be exhausting to try to work through the latest technologies and IoT devices that might help your business, and it’s definitely a resource drain. But when you work with an MSSP, you can rely on your partner’s knowledge and insights.
Managed Security Services with Flagship Solutions Group
In today’s dynamic threat landscape, your business can’t afford to take a reactive approach to cybersecurity. With a proactive security risk assessment, you can uncover vulnerabilities before they are exploited, mitigate potential risks, and safeguard your critical assets.
Flagship Solutions Group offers comprehensive Security Risk Assessments, taking a deep dive into multiple security domains. Our experts analyze your current security posture and provide valuable insights, actionable recommendations, and the next steps to fortify your defenses.

