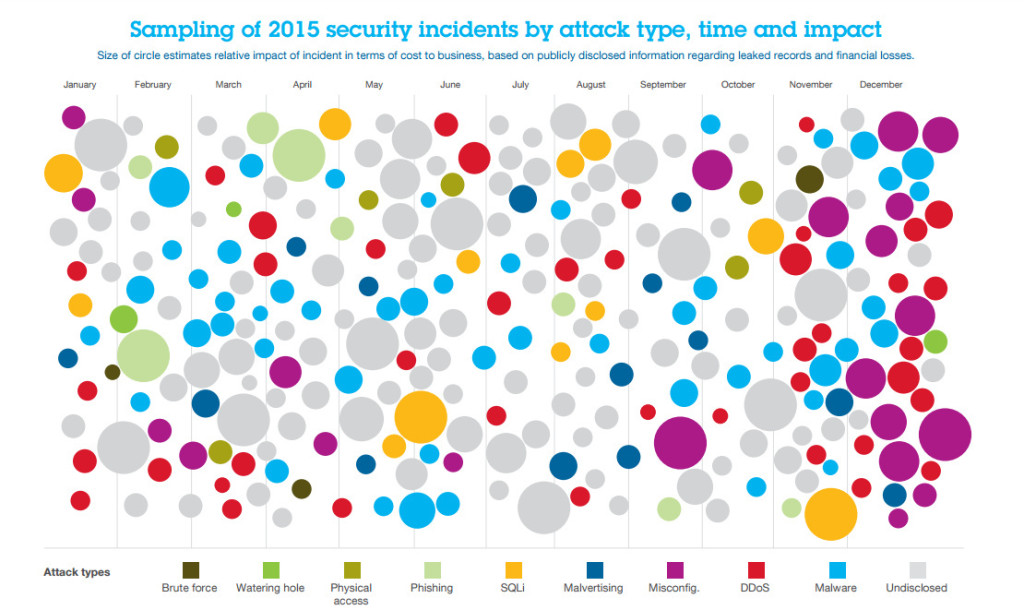
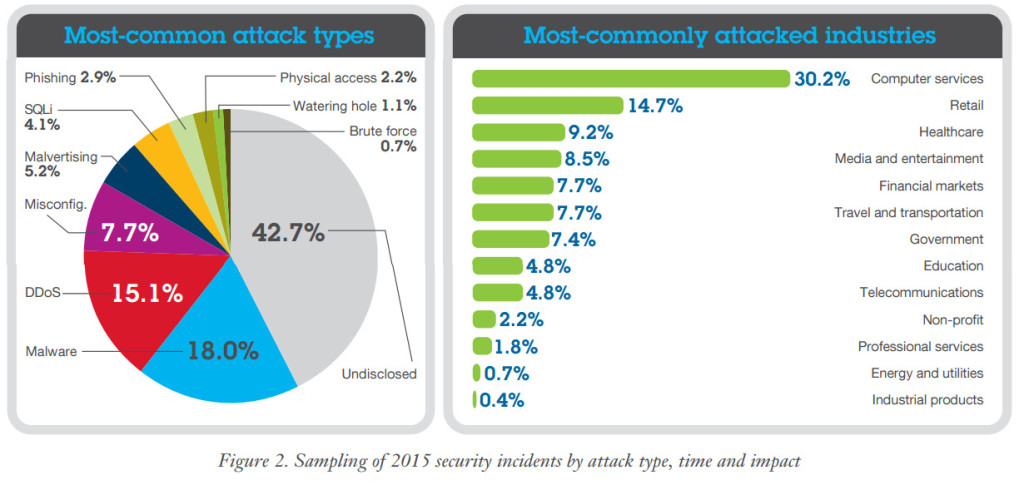
Looking back at cybercrime in 2015 leaves little doubt that the year was nothing short of epic. The IBM/Ponemon Institute report 2015 Cost of Data Breach Study put the average total cost of a data breach at $3.79 million, an increase from the 2014 figure of $3.52 million.
In 2014, IBM Security anticipated the following trends for 2015:
- Cybercrime breaking borders
- Rising card-not-present (CNP) fraud
- An escalation in the sophistication of mobile threats
- Wide use of anonymity networks and stronger encryption
- Burgeoning fraud methods for new payment schemes
- Biometrics becoming a target
These predictions not only materialized, but actually exceeded the forecast. We expect the situation to become very intense in 2016 as more organized crime groups step up their presence in the digital realms. The mob, digital edition It is safe to say that we have never before seen the magnitude and sophistication of online crime as we did in 2015—a trend that’s already proving to persist into 2016. This prompts us to ask: What is the one most significant factor contributing to cybercrime’s escalation in scale and sophistication?
The answer lies in the increasing involvement and investment of full-blown criminal organizations in digital crime, and the resulting increase in numbers of well-orchestrated operations such as Carbanak. (“Carbanak: How Would You Have Stopped a $1 Billion APT Attack?” Security Intelligence, 23 February 2015)
The mob, digital edition
These gangs operate much like businesses, leveraging connections, employing collaboration and deploying teams for different tasks. Organized cybercrime is no longer made up primarily of small factions, and the days of lone hackers are all but gone. Instead, nowadays we fight against motivated organizations that—like legitimate businesses—are divided into teams, employ highly experienced developers with deep knowledge, leverage connections and encourage collaboration. Also like businesses, these gangs are highly organized, managed by crime lords who fund the operation and deploy various types of troops to achieve their eventual success.
Given this highly organized structure, perhaps the level of sophistication shown in malicious code such as Shifu,( “Shifu: ‘Masterful’ New Banking Trojan Is Attacking 14 Japanese Banks,” Security Intelligence, 31 August 2015) for example, should be no surprise. After all, the security and risk management site CSO reports that the average age of a cybercriminal is an experienced 35 years, and 80 percent of blackhat hackers are affiliated with organized crime and work as part of groups. (Taylor Armerding, “Cybercrime: Much more organized,” CSO Online, 23 June 2015) In fact, the same article notes, according to some experts “disorganized cybercrime” no longer exists.
The inner workings of gang-controlled malware exposes the organization and order behind the scenes, with professional programming techniques built into the malware, as well as professional development processes such as change tracking, versioning and application security.
POS deserves a mention
Information security headlines throughout 2015 also often remarked upon the unprecedented modularity of malware that had been less complex before—for example, point-of-sale (POS) malware such as ModPOS, or the JavaScript-based ransomware known as Ransom32 that can be deployed across different platforms. It is no coincidence that malicious code is seeing such a hike in sophistication, however. The promise of a hefty return on investment (ROI) draws organized crime to fund them and lures brilliant minds into the dark world of digital crime.
Shifting from consumers to big business
If there was one trend that stretched across all cybercrime domains in 2015, it was the scaling up of the magnitude and breadth of each malware-related transaction and operation. Every type of malware cyber-attack last year—from ransomware to banking Trojans, and from cyber-extortion to targeted attacks—scaled up its per-hit quota. Cybercriminals accomplished this goal by shifting some of their focus from attacking individual consumers, to targeting businesses.
As they shifted to focus on larger rewards, malware groups such as Dyre updated their malicious code with new modules such as “pn32,” which is designed to harvest administrative user credentials for enterprise email servers. We suspect that this sort of development was not only part of the process of fraudulent transactions from the corporate account, but also was further designed to enable the gang behind Dyre to target victims with Business Email Compromised (BEC) fraud. (“Business E-Mail Compromise: An Emerging Global Threat,” Federal Bureau of Investigation, 28 August 2015)
BEC fraud occurs when blackhat hackers compromise business email or enterprise email servers, then use social engineering to send a credible-looking email to the company’s accountant or treasurer with instructions to promptly make a large wire transfer. The emails typically purport to come from the CEO or CFO, and sums involved can typically reach $1 million at a time. In the context of scaling up the magnitude of attacks by targeting businesses, two striking cases demonstrate just how brazen and well-organized cybercrime has become—first the Dyre Wolf attacks, which use the Dyre Trojan against corporate banking accounts, and second the Evil Corp. attack on Penneco Oil, which used the Trojan known as Dridex.
In each of these cases, malware operators combined the characteristics of a targeted attack with the abilities of Trojan-enabled online banking fraud. Subsequent conversations IBM researchers had with affected victim organizations made it clear that the cybercrime groups that launched these attacks prepared an elaborate social engineering scheme before the actual attempt.
Preparations included moving money from other, smaller accounts the company held to the account owned by the same company the cybercriminals planned to rob; establishing special toll-free numbers for the victims to call; assigning an eloquent, professional sounding “banker” with prior information about the account to speak to the victims; and setting up the type of mule accounts that could receive a large amount of money in one transaction without raising suspicion.
While every year in the past two decades showed an escalation in cybercrime, 2015 was particularly eventful. Attacks such as Carbanak, Dyre Wolf and Dridex on corporate bank accounts made 2015 stand out as some of the grandest digital crimes we have ever seen.
On to 2016…
As we kick off 2016, we expect the intensity of threats and increasing sophistication of malware to continue trending upward.
Flagship Solution Group along with IBM Security research teams can help you keep up to date on the trends that matter to your organization—as soon as they emerge. Schedule a consultation.
If you liked this blog, you might also like: Smarter Security, Smarter Everything
IBM Security: QRadar Intelligence and Ops
IBM's integrated solutions harness security-relevant information from across your organization, and use analytics and automation to provide context and help you detect threats faster, identify vulnerabilities, prioritize risks, perform forensics analysis and automate compliance activities. 
-
IBM QRadar Security Intelligence Solutions Grow As Your Needs Grow
-
Organizations today need integrated security intelligence solutions that can grow as their business grows, both in terms of size and capabilities. The IBM QRadar Security Intelligence Platform meets these requirements by providing an integrated security solution that is highly scalable, and can expand it’s capabilities to meet increasingly hostile security challenges. This short video describes how IBM Security QRadar delivers scalability, visibility, vulnerability management, risk management, and performs forensics analysis to help you quickly and efficiently detect and respond to security threats. To learn more, please visit http://ibm.co/1HNzm2n
-
Report: IBM X-Force Threat Intelligence Report 2016
-
In the modern era of mega breaches, there seems to be an ever-upward trend of more attacks, more leaked records and more varied threats. Yet, by the numbers, 2015 was not a complete disaster. While significant interruptions, shifts in perspective and challenges to the security industry continue to evolve, there are some areas of slowed growth and even improvement. This paper takes a look at some of the notable highlights from 2015 and makes some projections at what we might glean for the future.
-
How IBM Helps Secure the Cloud
-
IBM Security helps customers secure public, private and hybrid clouds. With IBM Security customers can manage user access to cloud applications and protect the data that lives in the cloud. Customers can use IBM Security products like QRadar to gain full visibility into security threats facing their organization.For more information, please visit http://ibm.co/1zlRM6Y
-
Benefits of Security Intelligence on Cloud
-
Watch this short video and listen to Vijay Dheap, IBM Global Product Manager for Security, describe the benefits of Security Intelligence on Cloud, a new offering from IBM. These include lowering costs, increasing efficiency, shifting from a CapEx to an OpEx model, and improving compliance and reporting. Vijay also touches on the advantages of incident forensics and the rapid analysis of security offenses. For more information, please visit http://ibm.co/1zlRM6Y
-
KocSistem Replaces Their SIEM & Deploys QRadar For Log Management & Regulatory Compliance
-
Many organizations are challenged with meeting regulatory compliance mandates. Watch this video and learn how Ko?Sistem, one of the largest IT services companies in Turkey, is complying with regulations using IBM Security QRadar. You will hear about how they removed a SIEM from another company and installed QRadar, and lowered costs, improved performance, and benefited from greater ease of use.For more information on QRadar, please visit: http://ibm.co/1DFd42q
-
The Next Era for Security – IBM QRadar Security Intelligence Platform
-
“IBM QRadar Security Intelligence Platform provides real-time transparency to see better into your organization than ever before,” says Steve Robinson, Vice President, IBM Security Division. Implementing the security information and event management (SIEM) dashboard, the IBM QRadar platform brings security operations teams full visibility through a single window. It also automates the tedious task of vulnerability management. Security teams can spend less time on manual tasks and more time on network security assessments. This means, according to Robinson, “QRadar will probably pay for itself right out of the gate.”For more information on Security Intelligence go to: http://ibm.com/software/products/us/en/subcategory/SWI60For more information on IBM Security: http://ibm.co/ibmsecurity
-
IBM Security Intelligence for the Cloud with QRadar
-
IBM QRadar Security Intelligence helps you monitor the cloud for security breaches and compliance violations using advanced security analytics. Using a flexible deployment architecture and connectors to popular cloud services, IBM QRadar Security Intelligence provides deep visibility of threats across both on-premise IT and hybrid cloud deployments.To learn more, please visit http://ibm.co/1DwamZk
-
How to Investigate Security Incidents Quickly and Easily
-
What’s behind a cyber attack? Gaining insight and clarity into the what, when and how of an enterprise security incident: IBM Security QRadar Incident Forensics helps you win the race against time when a security breach occurs by allowing you to rapidly and easily perform in-depth security incident investigations. It provides visibility and clarity to potentially malicious activity by thoroughly analyzing packets captured from your network, and in most cases can help resolve security incidents in minutes or hours instead of days or weeks. It is integrated with IBM Security QRadar solutions, allowing the same person who has visibility to logs and network flows to conduct searches and learn more about an incident. With QRadar Incident Forensics, security staffs can analyze many types of data, understand their relationships, re-trace the steps of an attacker, remediate damage, and reduce the chances of a recurrence. Learn more about QRadar Incident Forensics: http://ibm.co/QrSCg3
-
IBM Security QRadar and iSecure Work Together to Improve Customer Security
-
This short video describes the benefits that customers receive from the IBM Security QRadar and iSecure partnership. iSecure wraps their services around IBM’s QRadar products and helps clients address their security gaps. iSecure chose IBM because of the visibility QRadar provides to security exposures, and IBM’s continued investment in new capabilities such as vulnerability management, risk management, and incident forensics. iSecure also endorses IBM ability to provide a solution that combines multiple point products into a single, consolidated security solution.Learn more about IBM Security: http://ibm.co/ibmsecurity
-
Local Government Secures Their Data With QRadar
-
Securing people and funds is a challenge for the public sector. With these limited resources, IT departments must choose a security tool set that will be easy to implement as well as easy to manage. In this video, a local government explains why they chose IBM Security’s QRadar and how it has been a true asset to their work process.To learn more about QRadar, please visit http://ibm.co/1HNzm2n
-
Quickly Investigate & Resolve Security Events with QRadar Incident Forensics
-
When you make intelligent analytics part of your IT security strategy, you gain access to the tools to quickly identify and stop network security breaches, before real damage is done. IBM QRadar Incident Forensics helps security professionals reduce time spent on manual searches to identify a true threat, quickly analyze and stop the attack, and reconstruct the incident to gain the knowledge to prevent a similar attack in the future. To learn more, visit http://ibm.co/15NUhEI